flash
RAM
ROM
NVRAM
cisco certification 200-125 ccna exam preparation with practice questions and Answers
Which OSI layer manages data segments?
application layer
presentation layer
session layer
transport layer
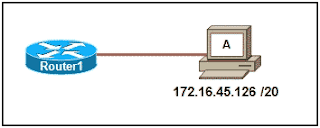
Refer to the exhibit. Which option correctly identifies the network address, range of host addresses, and the broadcast address for the network that contains host A?
Refer to the exhibit. Which option correctly identifies the network address, range of host addresses, and the broadcast address for the network that contains host A?
What is described by the network access layer of the TCP/IP model?
rules for packet acknowledgment, error recovery, and sequencing
rules for the handoff from the internet layer to the network access protocols
rules for how source and destination hosts exchange data between programs
rules for determining which processes can be used to route messages through an internetwork
rules for the handoff from the internet layer to the network access protocols
rules for how source and destination hosts exchange data between programs
rules for determining which processes can be used to route messages through an internetwork
Refer to the exhibit. A network technician wants to connect host A to the console of a Cisco switch to initialize the configuration. What type of cable is required for this connection?
straight-through cable
crossover cable
rollover cable
crossover cable
rollover cable
What can the user do from the command prompt, Router(config-line)# ?
Configure one of the network interfaces.
Configure one of the physical or virtual lines.
Verify the running configuration on the device.
Configure one of the physical or virtual lines.
Verify the running configuration on the device.
Which physical component is used to access and perform the initial configuration on a new unconfigured router?
Which physical component is used to access and perform the initial configuration on a new unconfigured router?
The tracert 10.1.3.2 command was issued on computer A. Computer A can ping other addresses on the local subnet. Computer A sent the first ICMP packet toward computer B with a TTL value of 1. A protocol analyzer that was running on computer B showed that the packet never reached its destination. Why did the packet not reach the destination?
The tracert 10.1.3.2 command was issued on computer A. Computer A can ping other addresses on the local subnet. Computer A sent the first ICMP packet toward computer B with a TTL value of 1. A protocol analyzer that was running on computer B showed that the packet never reached its destination. Why did the packet not reach the destination?
A user enters http://www.cisco.com/web1.htm in the address line of a browser. Which statement is true about this transaction?
The "http" portion indicates the protocol that is being used.
The "web1.htm" portion is the specific service name.
The retrieved web page will be displayed in URL code.
The "www.cisco.com" is the name of the web page file that is called
The "web1.htm" portion is the specific service name.
The retrieved web page will be displayed in URL code.
The "www.cisco.com" is the name of the web page file that is called
Refer to the exhibit. Communication for hosts X and Y is restricted to the local network. What is the reason for this?
Refer to the exhibit. Communication for hosts X and Y is restricted to the local network. What is the reason for this?
Refer to the exhibit. When host A sends a frame addressed for host D, which hosts will receive the frame?
Refer to the exhibit. When host A sends a frame addressed for host D, which hosts will receive the frame?
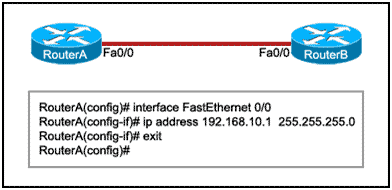
Refer to the exhibit. RouterB is configured properly. The Ethernet interface Fa0/0 of RouterA is configured with the use of the commands that are shown. However, a ping from the Fa0/0 interface of RouterA to the Fa0/0 interface of RouterB is unsuccessful. What action should be taken on RouterA to solve this problem?
Refer to the exhibit. RouterB is configured properly. The Ethernet interface Fa0/0 of RouterA is configured with the use of the commands that are shown. However, a ping from the Fa0/0 interface of RouterA to the Fa0/0 interface of RouterB is unsuccessful. What action should be taken on RouterA to solve this problem?
What two conclusions are evident from these commands? (Choose two.)
Users who attempt to connect to the console port of the router must enter a password.
The entries permit access through the console by the use of j1mdi2 as the password.
The entries eliminate the need for authentication.
Access through the console will be denied because the console configuration is incomplete.
The entries prevent passwords from being displayed as plain text.
The entries permit access through the console by the use of j1mdi2 as the password.
The entries eliminate the need for authentication.
Access through the console will be denied because the console configuration is incomplete.
The entries prevent passwords from being displayed as plain text.
Which two types of media can provide bandwidth up to 1 Gb/s? (Choose two.)
10 BASE-T
100 BASE-T
100 BASE-FX
1000 BASE-TX
1000 BASE-SX
100 BASE-T
100 BASE-FX
1000 BASE-TX
1000 BASE-SX
Refer to the exhibit. An employee wants to access the organization intranet from home. Which intermediary device should be used to connect the organization intranet to the Internet to enable this access?
Refer to the exhibit. An employee wants to access the organization intranet from home. Which intermediary device should be used to connect the organization intranet to the Internet to enable this access?
An organization has been assigned network ID 10.10.128.0 and subnet mask 255.255.224.0. Which IP address range can be used for this organization?
10.10.128.0 to 10.10.160.255
10.10.128.0 to 10.10.159.255
10.10.128.0 to 10.10.192.255
10.10.128.0 to 10.10.0.159
10.10.128.0 to 10.10.159.0
10.10.128.0 to 10.10.159.255
10.10.128.0 to 10.10.192.255
10.10.128.0 to 10.10.0.159
10.10.128.0 to 10.10.159.0
Refer to the exhibit. A technician is working on a network problem that requires verification of the router LAN interface. What address should be pinged from this host to confirm that the router interface is operational?
Refer to the exhibit. A technician is working on a network problem that requires verification of the router LAN interface. What address should be pinged from this host to confirm that the router interface is operational?
Which prompt represents the appropriate mode used for the copy running-config startup-config command ?
Switch-6J>
Switch-6J#
Switch-6J(config)#
Switch-6J(config-if)#
Switch-6J(config-line)#
Switch-6J#
Switch-6J(config)#
Switch-6J(config-if)#
Switch-6J(config-line)#
Refer to the exhibit. Host A attempts to establish a TCP/IP session with host C. During this attempt, a frame was captured with the source MAC address 0050.7320.D632 and the destination MAC address 0030.8517.44C4. The packet inside the captured frame has an IP source address 192.168.7.5, and the destination IP address is 192.168.219.24. At which point in the network was this packet captured?
Refer to the exhibit. Host A attempts to establish a TCP/IP session with host C. During this attempt, a frame was captured with the source MAC address 0050.7320.D632 and the destination MAC address 0030.8517.44C4. The packet inside the captured frame has an IP source address 192.168.7.5, and the destination IP address is 192.168.219.24. At which point in the network was this packet captured?
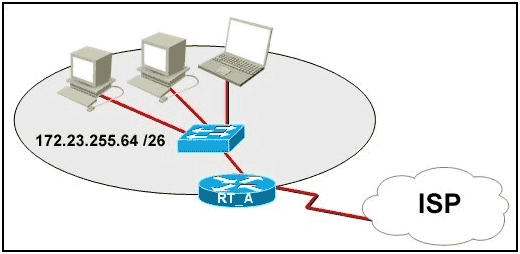
Refer to the exhibit. What function does router RT_A need to provide to allow Internet access for hosts in this network?
Refer to the exhibit. What function does router RT_A need to provide to allow Internet access for hosts in this network?
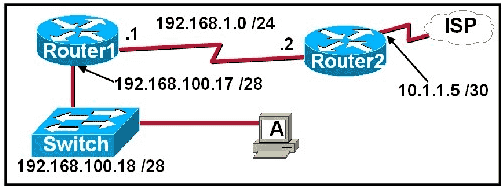
Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host A. What is a valid configuration for Host A?
Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host A. What is a valid configuration for Host A?
IP address: 192.168.100.19; Subnet Mask: 255.255.255.248; Default Gateway: 192.16.1.2IP address: 192.168.100.20; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.17
IP address: 192.168.100.21; Subnet Mask: 255.255.255.248; Default Gateway: 192.168.100.18
IP address: 192.168.100.22; Subnet Mask: 255.255.255.240; Default Gateway: 10.1.1.5
IP address: 192.168.100.30; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.1.1
IP address: 192.168.100.31; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.1
When must a router serial interface be configured with the clock rate command?
when the interface is functioning as a DTE device
when the interface timers have been cleared
when the connected DTE device is shut down
when the interface is functioning as a DCE device
when the interface timers have been cleared
when the connected DTE device is shut down
when the interface is functioning as a DCE device
Which subnet mask would be assigned to the network address of 192.168.32.0 to provide 254 useable host addresses per subnetwork?
255.255.0.0
255.255.255.0
255.255.254.0
255.255.248.0
Refer to the exhibit. Assume that all devices are using default settings. How many subnets are required to address the topology that is shown?
Refer to the exhibit. Assume that all devices are using default settings. How many subnets are required to address the topology that is shown?
Which option identifies the primary interface which would be used for initial configuration of a Cisco router?
AUX interface
Ethernet interface
serial interface
console interface
What are three common methods for setting a UTP Ethernet port to MDI or MDIX operation? (Choose three.)
direct configuration of the device
cable color code association
cable selection and configuration
use of cable testers to determine pinouts
the enabling of the mechanism to electrically swap the transmit and receive pairs
the automatic detection and negotiating of MDI/MDIX operation of the port
What type of network cable is used between a terminal and a console port?
cross-over
straight-through
rollover
patch cable
Refer to the exhibit. A network technician has been allocated the 192.168.1.0/24 private IP address range for use in the network that shown in the exhibit. Which subnet mask would be used to meet the host requirements for segment A of this internetwork?
Refer to the exhibit. A network technician has been allocated the 192.168.1.0/24 private IP address range for use in the network that shown in the exhibit. Which subnet mask would be used to meet the host requirements for segment A of this internetwork?
255.255.255.128255.255.255.192
255.255.255.224
255.255.255.240
255.255.255.248
To establish a console connection from a computer to a Cisco router, which cable wiring option would be used?
crossover cable
straight through cable
rollover cable
V.35 cable
Refer to the exhibit. A student is setting up a home network primarily used for extensive file transfers, streaming video, and gaming. Which network device is best suited to these types of activities in the topology shown?
Refer to the exhibit. A student is setting up a home network primarily used for extensive file transfers, streaming video, and gaming. Which network device is best suited to these types of activities in the topology shown?
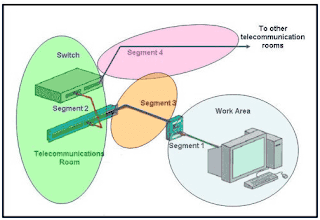
Refer to the exhibit. Which three statements identify the type of cabling that would be used in the segments that are shown? (Choose three.)
Refer to the exhibit. Which three statements identify the type of cabling that would be used in the segments that are shown? (Choose three.)
What does the term “attenuation” mean in data communication?
loss of signal strength as distance increases
time for a signal to reach its destination
leakage of signals from one cable pair to another
strengthening of a signal by a networking device
Refer to the exhibit. What destination IP address will PC1 place in the header for a packet destined for PC2?
Refer to the exhibit. What destination IP address will PC1 place in the header for a packet destined for PC2?
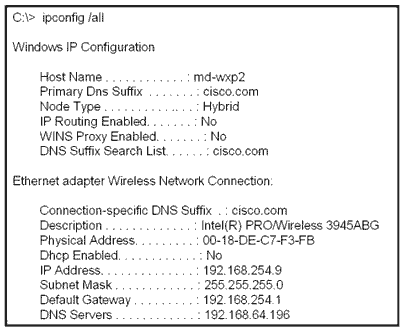
Refer to the exhibit. Based on the IP configuration shown, what would be the result of Host A and Host B attempting to communicate outside the network segment?
Refer to the exhibit. Based on the IP configuration shown, what would be the result of Host A and Host B attempting to communicate outside the network segment?
both host A and B would be successful
host A would be successful, host B would fail
host B would be successful, host A would fail
both Host A and B would fail
Which three types of connectors are commonly associated with Cisco’s V.35 serial cables? (Choose three.)
RJ 11
DB 60
Winchester 15 pin
DB 9
smart serial
RJ 45
Refer to the exhibit. Which three statements are true about the exhibited topology? (Choose three.)
Hosts B and C are in the same subnet.
Five broadcast domains are present.
Host B is using a crossover cable to connect to the router.
Four broadcast domains are present.
Five networks are shown.
Host B is using a rollover cable to connect to the router.
Refer to the exhibit. A student working in the lab selects a cable that is wired as shown. Which connection types can successfully be made with this cable? (Choose two.)
connecting a PC to a router’s console port
connecting two routers together via their fast ethernet ports
connecting two switches together at gigabit speeds
connecting a PC to a switch at Gigabit Ethernet speeds
connecting two devices with the same interface type at Fast Ethernet speeds
A company is planning to subnet its network for a maximum of 27 hosts. Which subnet mask would provide the needed hosts and leave the fewest unused addresses in each subnet?
255.255.255.0
255.255.255.192
255.255.255.224
255.255.255.240
255.255.255.248
What are two common methods for setting a UTP Ethernet port to MDI or MDIX operation? (Choose two.)
cable color code association
cable selection and configuration
use of cable testers to determine pinouts
the automatic detection and negotiating of MDI/MDIX operation of the port
the enabling of the mechanism to electrically swap the transmit and receive pairs
cable selection and configuration
use of cable testers to determine pinouts
the automatic detection and negotiating of MDI/MDIX operation of the port
the enabling of the mechanism to electrically swap the transmit and receive pairs
Refer to the exhibit. A network administrator has decided to use packet capture software to evaluate all traffic from the student subnet on the way to the Internet. To ensure that all packets are captured, what network device should be used to connect the monitoring station to the network between R1 and R2?
Subscribe to:
Comments (Atom)
Popular Posts
-
Administrative distance refers to the trustworthiness of a particular route. A router first installs routes with higher administrative dis...
-
Refer to the exhibit. Routers R1 and R2 are directly connected via their serial interfaces and are both running the EIGRP routing protocol...
-
Load balancing occurs when a router sends the same packet to different destination networks. Load balancing occurs when a router sends the...
-
greater distances per cable run lower installation cost limited susceptibility to EMI/RFI durable connections greater bandwidth potential e...
-
service provider edge enterprise WAN applications and devices services module
-
What is a component of a routing table entry? the MAC address of the interface of the router the destination Layer 4 port number the ...
-
The host is unable to communicate on the local network. The host can communicate with other hosts on the local network, but is unable t...
-
This router only has two interfaces. The router interfaces are not operational yet. This router is configured to forward packets to re...
-
They will share all routes saved in NVRAM prior to the power loss with their directly connected neighbors. They will multicast hello packe...

















.jpg)



